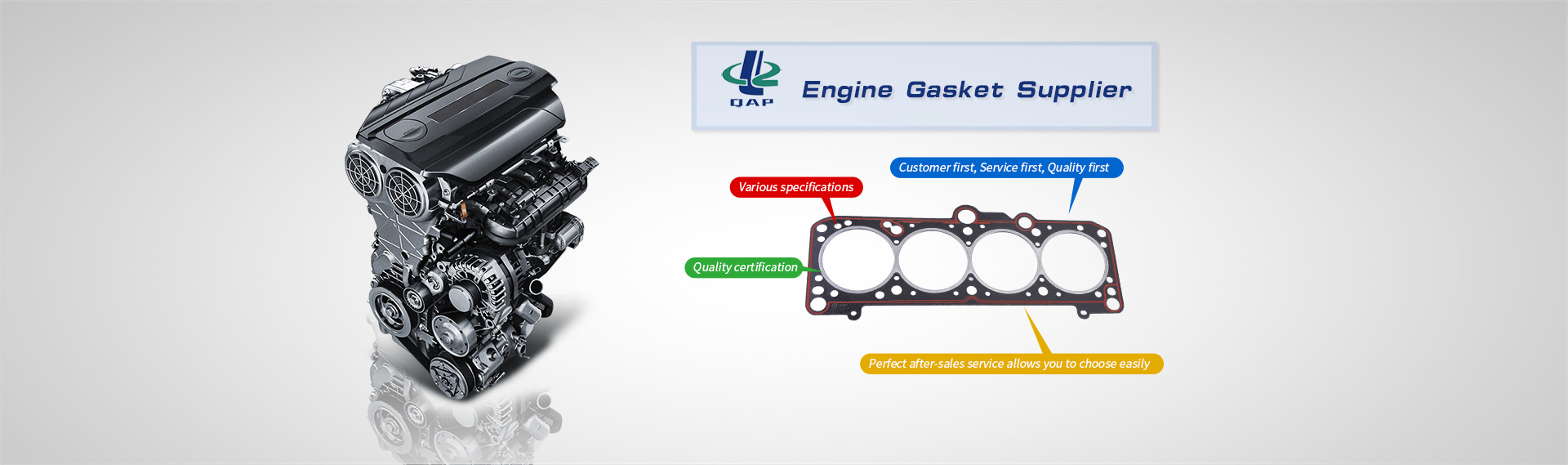
Wuhu Qilu Auto Parts Co., Ltd

NEWS Information
How does the "car network" encounter the "hacker" security problem?
Source:
|
Author:it-101
|
Published time: 2015-04-03
|
1139 Views
|
Share:
In any Internet cafe in the province, if someone is playing vulgar online games, the video management system of the provincial Department of Culture will be able to see clearly, and will take corresponding measures and punishment to the Internet cafe violating the rules in the first time.
As an important node of the Internet of Everything, the car is no
longer an independent mechanical entity, but a super-powerful mobile
terminal, but the security risks that come with it are increasingly
prominent. At the Third World Intelligence Conference held in Tianjin,
the topic of “black” was triggered by the conference. Unlike computers
and mobile phones, if a car is "black", it will lead to information
leakage and damage to property, which will endanger personal safety. So,
how to solve the security problem in the era of Internet of Vehicles?
The car is "black" is not a movie scene
The car network was hijacked by hackers and it was not just a scene in
the movie. In reality, information security incidents have occurred in
the field of intelligent networked vehicles. According to the "2018
Intelligent Networked Automotive Information Security Annual Report"
released by 360, in the past year alone, there have been 14 intelligent
networked car information security incidents, including 5 data breaches
and 9 car cracking incidents.
According to industry insiders, after hackers discovered that there is a
loophole in the embedded embedded operating system or vehicle hardware
and software, they use a variety of different system vulnerabilities to
carry out attacks through complex technical means, so that they can
steal the vehicle, but they can partially control the driving state.
car. As Tesla, the leader of the intelligent network car, there have
been 150 cars that have been hacked and stolen.
Xin Kezhen, chairman of Unicom's Zhiwang Technology Co., Ltd., said
that China is the world's largest auto market and the world's largest
mobile Internet market. The combination of the two makes China naturally
have a fertile Internet of Vehicles. As the open connection of vehicles
has gradually increased, data exchange between related equipment
systems has become closer, and Internet security threats such as network
attacks, Trojan viruses, and data theft have gradually penetrated into
the field of vehicle networking.
Why is the car easy to be "black"?
The reporter learned that many manufacturers are now deploying Internet
cars, and they have subtly shifted people's attention to consumption,
entertainment, and practicality, and there are few questions about car
safety risks.
Zhang Yanan, director of the software testing department of China
Automotive Technology and Research Center Co., Ltd., said that
automotive information security currently faces ten major risks,
including unsafe cloud interfaces, unauthorized access, backdoors in the
system, unsafe vehicle communication, The vehicle network has not been
safely isolated.
"Unscrupulous people can invade the server to tamper with the data
content and destroy the hard disk data through the risk of these
vulnerabilities; enable the car to open the door, power on, ignite, etc.
if the owner does not operate the car; cause the car entertainment
system firmware through the exposed debug port Attacked and extracted,
etc." Zhang Yanan said.
"The problem of car networking is left in the process of combining the
car with the Internet, but the hidden dangers of security
vulnerabilities will cause pains and lessons. This is the consequence of
the low investment and insufficient attention of the automakers." An
industry insider admitted that Some car dealers are still old-fashioned,
only paying attention to traditional security and neglecting
information security.
Zhou Hongyi, Chairman and CEO of 360, believes that “everything needs
to be interconnected and everything is programmable.” This means that
the physical world and the virtual world have been opened, the
boundaries between online and offline are disappearing, and attacks from
cyberspace will penetrate virtual space. Directly affect the security
of the physical world. Coupled with the development of the Internet of
Things, networked smart devices can grow by as much as 10 billion, and
each smart device can become an entry point for attacks.
How to say "no" to hackers in the era of car networking
“China has carried out network security testing and evaluation, and
guided relevant testing organizations to build vehicle network security
testing and verify the environment.” Fujing Advertising, the director of
the Network and Data Security Division of the Network Security
Administration of the Ministry of Industry and Information Technology,
the relevant departments are aimed at autonomous driving and vehicle
Safety inspection of parts and components, as well as inspection and
evaluation of the Internet of Vehicles platform, and prevention of the
risk of sensitive data leakage such as illegal control of location
information.
Fu Jingguang said that in order to ensure the healthy development of
the vehicle networking industry, the relevant state departments will
promote the integration of key equipment of the vehicle networking
network into the national network key equipment safety testing and
certification system, and accelerate the construction of monitoring and
early warning, information sharing, emergency response and other
mechanisms for vehicle network security. Standardize the disclosure of
vulnerabilities and continuously improve the level of situational
awareness and emergency response.
Some netizens believe that although there is no accident that has been
caused by the use of loopholes, it is hoped that it will prevent
problems before they happen. For the safety of the Internet of Vehicles,
all aspects of technology, vehicle management, industry laws and
standards need to be further improved.
Gao Hesheng, deputy secretary of the Party Committee of China
Automotive Technology and Research Center Co., Ltd., said that
automobile information security is crucial, but the information security
field as a whole faces problems such as insufficient talent capacity,
lack of technology and shortage of tools. The development of intelligent
networked automobile industry has been affected to a certain extent.
influences. With the continuous development of “new four” (ie,
electrification, intelligence, networking, and sharing), public opinion
sharing and analysis will become an important means to solve automotive
information security problems. (Reporter Zhou Runjian Fu Guangyu)
Copyrights © 2022 Wuhu Qilu Auto Parts Co., Ltd All Rights Reserved Design by JingZhou Tech